When Microsoft 365 Copilot enters the picture, everything your users can access becomes part of the content Copilot can draw from. That means documents with overly broad permissions, accidental shares, and legacy access settings are all fair game. If something was shared “just for convenience,” Copilot won’t care. It will surface that content confidently, whether or not the audience was meant to see it.
In this post, you’ll learn how to identify overshared content in Microsoft 365, fix excessive access in SharePoint and Teams, and tighten your tenant’s external sharing policies before Copilot makes those gaps visible to everyone.
What Is Oversharing in Microsoft 365?
Oversharing happens when internal or sensitive content is made accessible to a wider audience than necessary. In Microsoft 365, this often includes:
- SharePoint sites marked as public
- Microsoft Teams with unrestricted membership
- Sharing links set to “Anyone” or “People in your organization”
- Permissions using “Everyone” or “Everyone Except External Users” (EEEU)
- Forgotten guests with lingering access to confidential files
These sharing configurations often fly under the radar, until Copilot starts using that data in summaries, emails, or documents. Then it becomes very obvious, very fast.
Step 1: Audit Public SharePoint Sites and Teams
Believe it or not, in the SharePoint Admin Center you cannot filter public or private sites. And no one enjoys manually opening each site to check the privacy setting. Since every SharePoint site has a M365 group connected to it, you can check the setting in the group. This is possible in the Exchange Admin Center.

If you click Export, you create a csv file where you can filter on M365 Groups and Group privacy.
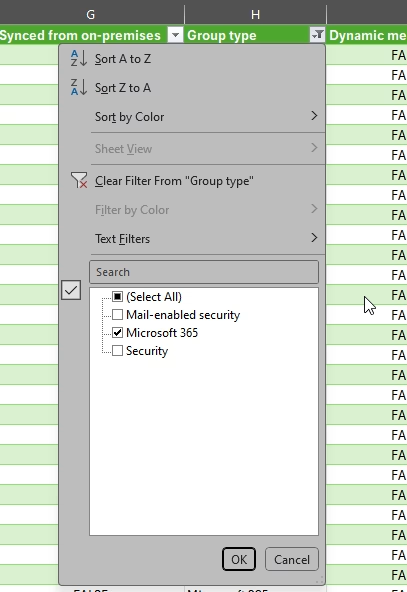
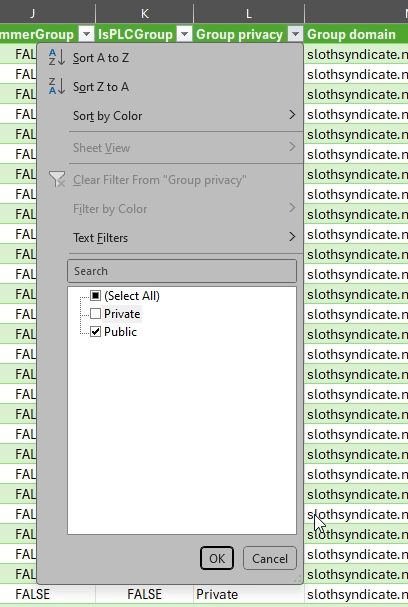
Next, head to the Microsoft Teams admin center. Here it is also easiest to create an export to csv file.


Sort your teams by privacy setting and identify any that are open to the organisation by default. Adjust those teams to private where appropriate and remove unnecessary members.
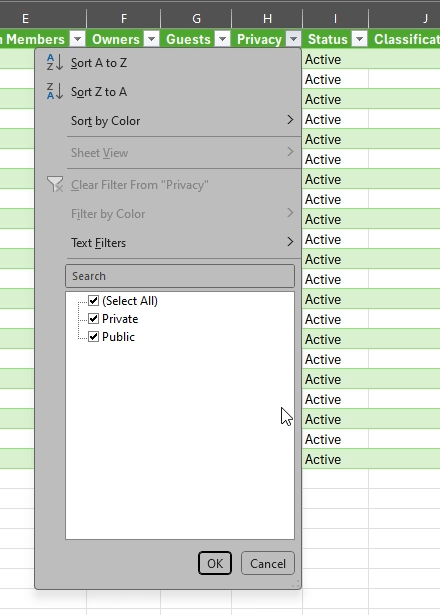
Step 2: Check Sharing Defaults and External Access
In the SharePoint admin center, check your organisation-wide sharing settings under Policies > Sharing. Content sharing should be set to at least “New and existing guests”. This prevents the selection of “Anyone with the link” for sharing.

The default link type should be set to “Specific people.” This ensures users cannot share files with the whole organisation or anonymous users unless explicitly changed.

Public SharePoint sites have “Everyone except external users” as group. By converting your public sites to private, this group gets removed.
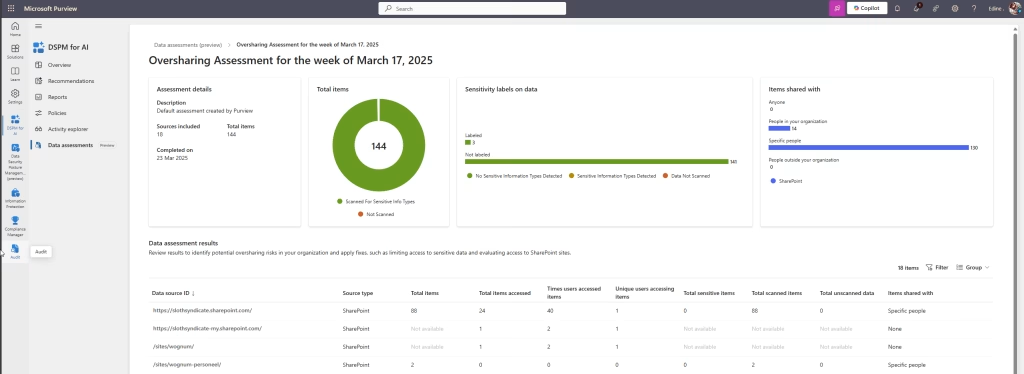
Step 3: Use SharePoint Advanced Management or DSPM For AI
If your tenant includes SharePoint Advanced Management or Microsoft Purview Data Security Posture Management (DSPM) for AI, use the available insights and dashboards to flag oversharing risks.
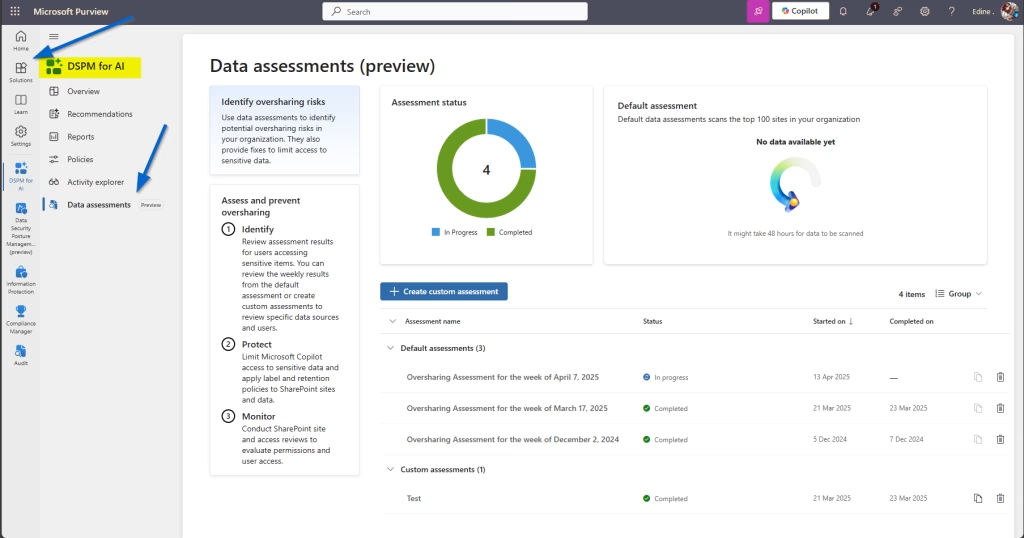
Look for:
- Sites with more than 100 users and no sensitivity label
- High guest access volume
- Anonymous sharing links with long or no expiration
- Content with sensitive data exposed to broad audiences
Prioritise clean-up on sites with business-critical content or active collaboration.
Step 4: Revoke Unnecessary Sharing Links
Even with good policies in place, old sharing links stick around. In the Microsoft Purview portal or the SharePoint admin center, generate a sharing report to identify files shared with “Anyone” or links that haven’t been used in a long time.
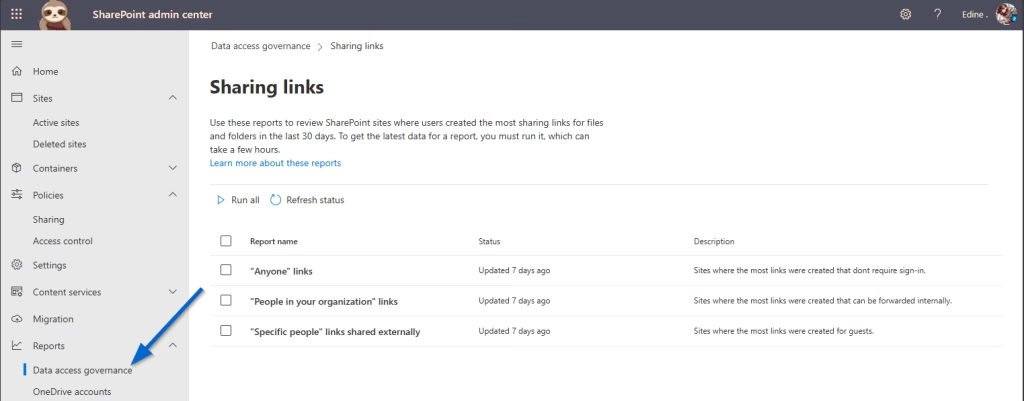
Remove expired, inactive, or high-risk sharing links. Notify content owners about the change and encourage re-sharing using specific people links.
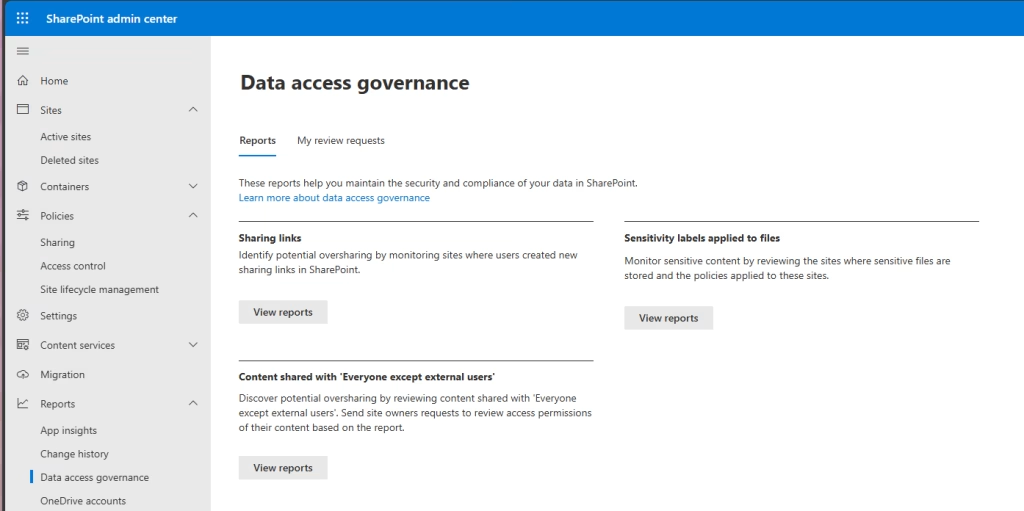
If you have access to SharePoint Advanced management, you see one more Data access governance report option, this being “Content shared with Everyone except external users”.
Step 5: Educate Site Owners and Teams
Governance tools will get you only halfway there. Users and site owners need to understand the impact of their sharing choices.
Create a simple guide or short training session explaining:
- What “oversharing” means in Microsoft 365
- Why Copilot can amplify those risks
- When and how to use private sites and sensitivity labels
- The importance of removing unnecessary access after a project ends
Step 6: Review and Monitor Sharing Regularly
Oversharing is not a one-time fix. Set up regular audits for your most active sites. Track changes to public site settings, guest access invitations, and sensitivity label usage. Make this part of your quarterly security or compliance check-up.
If you use Microsoft Purview, review activity trends and risk indicators through the dashboard. It will show you who is sharing, what is being shared, and where policies are not being followed.
How Oversharing Impacts Microsoft 365 Copilot
Copilot does not differentiate between “intended access” and “actual permissions.” If a user can access the content, Copilot will use it in responses, summaries, and insights. That includes legacy content, old project files, and anything shared with large groups by default.
Oversharing can lead to:
- Confidential data showing up in the wrong user’s Copilot prompt
- Loss of trust in Copilot’s accuracy
- Accidental breaches or compliance violations
Fixing access issues now gives you more confidence when Copilot rolls out.
Your Action List Before Copilot Goes Live
- Audit public SharePoint sites and Teams
- Adjust organisation-wide sharing settings
- Disable EEEU from the people picker via PowerShell
- Use advanced tools like DSPM to flag and fix risks
- Remove outdated sharing links
- Train users and set expectations
- Schedule recurring audits
Before Copilot Shines a Light on It
Microsoft 365 Copilot is incredibly helpful, but it does not filter out embarrassing or risky data. If the user has access, Copilot does too. By cleaning up oversharing now, you protect your organisation’s reputation, improve Copilot’s usefulness, and build a more secure digital workplace.
Next up, we’ll dive into Sensitivity Labels and how they add a second layer of control, even when permissions slip through the cracks.

